1- CAESAR CIPHER METHOD
(Monoalphabetic substitution cipher)
* In the period of the Roman Empire(100BC—44BC), famous leader Julius Caesar communicated with his forces with this encryption method. Important military messages were hidden in this way for many years and changed the course of wars.
* Although
it is easy to break this cipher in today's conditions, it has provided secure communication for a long time
when it was used.
* Caesar
used the encryption tool called Caesar disk to make these shifts practically.
* Curriculum
topics related to Caesar Cipher/ Aim: Factorial, probability (permutation), modular arithmetic...We want
to increase your gains on these issues with Caesar encryption activities. You
will experience interdisciplinary learning with history, mathematics,
informatics, english.
* I think
you say how? Let's start learning!
HOW DOES IT WORKS?
* Caesar
cipher is the technique of creating encrypted text by shifting the letters of
the alphabet . Therefore, it is also called shift cipher.
* This
cipher works by shifting the the letters in the alphabet by "k" unit
. "k" is the key.
EXAMPLE:
ENCRYPTION
*If you want
to encrypt “ETWINNING” word with key “3”.
First of
all, you need to replace each letter of the alphabet with the 3rd letter after
it.
You can see below cipher alphabet for key 3.
|
CipherAlphabet |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|
PlainAlphabet |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
Method: Caesar, Key: 3, Plaintext: ETWINNING, Ciphertext:HWZLQQLQJ
DECRYPTION
If you want
to decrypt“RDXYJWNTZX”word for key 5
First of
all, you need to replace each letter of the alphabet with the 5rd letter before
it.
|
CipherAlphabet |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|
PlainAlphabet |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
Method:Caesar,Key:5,Ciphertext:
RDXYJWNTZX, Plaintext: MYSTERIOUS
MIXED CAESAR CIPHER METHOD
The
difference from Caesar method is that the key is not a number, but a word. When
creating the encrypted alphabet, the key is written first and then the
remaining letters of the alphabet are used.
EXAMPLE:
ENCRYPTION
If you want
to encrypt “PROJECT” word with key “FRUIT”.
Firstly you’ll
write the key word. After than you’ll write the other letters in the alphabet(
except the letters of the keyword).Via this way you’ll mixed the cipher
alphabet.You can see below cipher alphabet.
|
PlainAlphabet |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|
CipherAlphabet |
F |
R |
U |
I |
T |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
G |
H |
J |
K |
L |
M |
N |
O |
P |
Q |
S |
Method:MixedCaesar,Key:FRUIT,Plaintext:PROJECT,Ciphertext: GJEZTUL
DECRYPTION
If we want
to decrypt “ZCVYC”word for key “VEGETABLE”
Similarly
you can create table below.
|
PlainAlphabet |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|
CipherAlphabet |
V |
E |
G |
T |
A |
B |
L |
M |
N |
O |
P |
Q |
R |
S |
U |
W |
X |
Y |
Z |
C |
D |
F |
H |
I |
J |
K |
Then if you replace each letter with it's equivalent in the table, you will get plain text“START”
Method:Mixed
Caesar,Key:VEGETABLE,Ciphertxt:ZCVYC,Plaintext:START
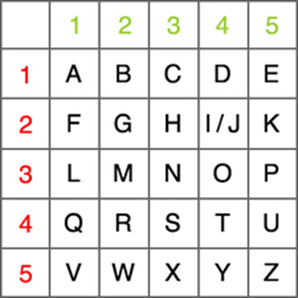
2-POLYBIUS CIPHER METHOD
(Monoalphabetic substitution cipher)
* It is a simple method used in ancient Greek times. It was developed by the famous historian Polybius(150 BC).
* It is a
method that converts letters to numbers
with square checkboards.
* The
original version is in the form of a 5x5
square (Greek alphabet)
* Square
size changes according to the number of letters in the alphabet. For example, a 7x7 matrix is required for the
Japanese alphabet.
* Below you can see to the standart
version adapted to the English alphabet (we will use this).
*Curriculum topics related to Polybius encryption/ Aim: Matrix, Probablity, Permutation.We want to increase your gains on these issues with Polybius encryption activities.
EXAMPLE
* If you
want to encrypt the ETWINNING ;
Only you
will change letters with numbers.Every letter
represents where it is located. For example, the letter E is denoted by
15. Similarly, if other letters are replaced with numbers, the cipher text
"154452243333243322" is obtained.
Method:Polybius ,Plaintext:ETWINNING,
Ciphertext: 154452243333243322
* Cipher
texts are also easily deciphered with the help of squares.
MIXED POLYBIUS CIPHER METHOD
Ciphers
which have a key are always more
stronger. Because they confuse the order of the letters in the alphabet.
EXAMPLE
İf you want
to encrypt "STAY HEALTHY" plain text, with POLYBIUS key;
* Firstly
you will write the key in the square.
* Then you
will continue other letters of the alphabet and fill the square.( Attantion!
use each letter only ones)
* You will get the table below.
* Finally
you will change each letter with corresponding number. And you will find the
cipher text " 23512414 35322413513514"
Method:Mixed Polybius ,Plaintext:STAY
HEALTY, Key: POLYBIUS,
Ciphertext: 23512414 35322413513514
* Cipher
texts are also easily deciphered with the help of squares.
3- AFFINE CIPHER METHOD
(Monoalphabetic substitution
cipher)
* We will
see in a moment how functions and
modular arithmetic in particular
are used for this encryption.
* This
encryption type which was used at various times in the past, is also the basic of today's encryption.
* Curriculum
topics related to Affine Cipher/ Aim : Linear functions, modular arithmetic,
prime numbers, composite numbers, between prime numbers,divisibility, common
divisors (You can clik links and then see basic properties of this math
subjects). We want to increase your gains on these issues with Affine
encryption activities. You will experience interdisciplinary learning with
history, mathematics, informatics, geography, English.
EXAMPLE
ENCRYPTION
Encryption
is done according to a linear function
f(x)=ax+b (mod m)
* m is the
number of letters in the alphabet used.
* a and b constans are the keys to the cipher.
* x is the
number represented by the letter in plain text.
* f (x) is
the value that creates the encrypted text.
* mod is moduler arithmetic.
For example,
let's convert the plain text "AFFINE CIPHER" in to ciphertext
according to the key (a, b) = (5,8). Let's give numbers to letters, starting
from 0 first.
|
PlainAlphabet |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|
CipherAlphabet |
0 |
1 |
2 |
3 |
4 |
5 |
6 |
7 |
8 |
9 |
10 |
11 |
12 |
13 |
14 |
15 |
16 |
17 |
18 |
19 |
20 |
21 |
22 |
23 |
24 |
25 |
f(x)=5x+8
(mod 26) function.
For example
we can make for "N"
N=13
f(13)=5.13+8=73
73=21 (mod
26), (The remainder from the division of
73 with 26 is 21)
f(13)=21
(mod 26)
21= V
So, the
letter N in plain text corresponds to the letter V in cipher text. If the
values corresponding to the other letters are found one by one, the following
table is obtained.
|
Plaintext |
A |
F |
F |
I |
N |
E |
|
C |
I |
P |
H |
E |
R |
|
x |
0 |
5 |
5 |
8 |
13 |
4 |
|
2 |
8 |
15 |
7 |
4 |
17 |
|
5x+8 |
8 |
33 |
33 |
48 |
73 |
28 |
|
18 |
48 |
83 |
43 |
28 |
93 |
|
5x+8 (mod 26) |
8 |
7 |
7 |
22 |
21 |
2 |
|
18 |
22 |
5 |
17 |
2 |
15 |
|
Ciphertext |
I |
H |
H |
W |
V |
C |
|
S |
W |
F |
R |
C |
P |
Method: Affine cipher, Key=(5,8),
Plaintext=AFFINE CIPHER, Ciphertext= IHHWVC SWFRCP.
DECRYPTION
If we want
to decrypt the ciphertext "IHHWVC
SWFRCP"
We have to do the reverse transaction. f (x),
inverse of the function
f-1 (x) =
(x-8) / 5
We need to
find the equivalent of this function in mod 26 . To remove the denominator, we
need to expand the fraction by a number to make the denominator 1 in mod 26.
This number is 21.
f-1 (x) =
21. (x-8) / 21.5
= 21 (x-5) / 105
= 21 (x-8) /1
= 21 (x-8)
f-1 (x) = 21 (x-8), (mod 26)
So we will
use is this function for decryption.
Let's decrypt IHHWVC SWFRCP with this function.
For example,
we can do for letter "C"
C=2
f-1 (x) = 21
(x-8)
f-1 (2) = 21
(2-8)
= - 126
To find the
equivalent of -126 in (mod 26) we need to add a multiple of 26.
-126 + 5.26
= -126 + 130 = + 4 = E
So, the
letter C in cipher text corresponds to the letter E in plain text . If the
values corresponding to the other letters are found one by one, the following
table is obtained.
|
Plaintext |
I |
H |
H |
W |
V |
C |
|
S |
W |
F |
R |
C |
P |
|
x |
8 |
7 |
7 |
22 |
21 |
2 |
|
18 |
22 |
5 |
17 |
2 |
15 |
|
21(x-8) |
0 |
-21 |
-21 |
294 |
273 |
-126 |
|
210 |
294 |
-63 |
189 |
-126 |
147 |
|
21(x-8) (mod 26) |
0 |
5 |
5 |
8 |
13 |
4 |
|
2 |
8 |
15 |
7 |
4 |
17 |
|
Ciphertext |
A |
F |
F |
I |
N |
E |
|
C |
I |
P |
H |
E |
R |
4- PERMUTATION CIPHER METHOD
(Monoalphabetic Transposition Cipher)
* Curriculum topics related to Permutation Cipher:/Aim Permutation function, matrix.We want to increase your gains on these issues with Permutation encryption activities.You will experience interdisciplinary learning with history, mathematics, informatics, English.
EXAMPLE
ENCRYPTION
If you want
to encrypt plaintext "COME TO THE
USUAL PLACE TONIGHT"
with
(12345-43125) permütation and "CLASS" key.
Firsly you
will divide the plaintext into pieces the length of the key. Our key
"CLASS" have 5 letter so it's lenght 5. You will divide the plain
text into five letter parts.(The keyword only tells us to divide the plain text
into groups of how many letters).
COMET OTHEU
SUALP LACET ONIGH Txxxx (Instead of missing letters, x is written)
You have
split the plain text into six parts. So you'll need six row.The number of
columns should be 5 as the length of the key. Then you will write the given
permutation first line, and the parts of the plaintext on the other lines in
order.
|
4 |
3 |
1 |
2 |
5 |
|
C |
O |
M |
E |
T |
|
O |
T |
H |
E |
U |
|
S |
U |
A |
L |
P |
|
L |
A |
C |
E |
T |
|
O |
N |
I |
G |
H |
|
T |
x |
x |
x |
x |
Method:Permutation, Key= CLASS,Permutation=(12345-
43125),
Plaintext=COME
TO THE USUAL PLACE TONIGHT, Ciphertext= MEOCTHETOUALU SPCEALTIGNOHxxxTx
DECRYPTION
If you want to decrypt cipher text
"MEOCTHETOUALUSPCEALTIGNOHxxxTx"
with
(12345-43125) permütation and "CLASS" key.
You have to look from invers to permutation.
So, you will use inverse permutation (12345-34215) permutation.The other steps
are similar to encryption. You will divide the cipher text into the length of
the key.
MEOCT HETOU
ALUSP CEALT IGNOH xxxTx
|
3 |
4 |
2 |
1 |
5 |
|
M |
E |
O |
C |
T |
|
H |
E |
T |
O |
U |
|
A |
L |
U |
S |
P |
|
C |
E |
A |
L |
T |
|
I |
G |
N |
O |
H |
|
x |
x |
x |
T |
x |
You will then rewrite each row in the order that the
permutation indicates.You will find ciphertext
"COMETOTHEUSUALPLACETONIGHTxxxx"
We used x's to fill blanks, they are unnecessary. Separating
words is up to you in this encryption:)
Finally we achieve
"COME TO THE USUAL PLACE TONIGHT"
Simple columnar transposition
(also called column permutations cipher)
– is a cryptographic technique that modifies the order of the letters of a previously written text in a table.We will use a full simple columnar transposition according to the key (i.e. it uses the keyword and the table, which we fill with X characters so that all cells in the table are filled).
To specify the size of the table, it is important to know the keyword, which indicates the number of columns in the table. Each letter of the keyword is assigned a number in alphabetical order, if a letter occurs more than once in a word, the smaller value will be given to the character that appears first. For example:
The key obtained in this way is written into the header of the table, which has the same number of columns as the number of digits. Under the password, we write the plaintext without spaces. If there are any spaces left in the last row of the table fields, we fill in the plaintext with random characters so that the table is complete (in this case, the character X).
PLAINTEXT:
THIS IS THE CODE FOR JANUARY ACTIVITIES ORGANIZED BY THE CZECH REPUBLIC
The cipher text is written in columns from 1 to n, where n is the length of the password. In our case, n = 7. Finally, we divide and write the ciphertext into groups of 5 characters.
CIPHERTEXT:
IDNTS ZEEXT HORIG BEBSE UIOEC PXICJ AINTH ISOAC EIHRC HERYT AYCLT FAVRD ZUX
Message decryption
The recipient of the encrypted message calculates the length of the text and divides it by the length of the keyword. This gives the number of rows in the table, the number of columns is given by the number of characters of the keyword. The decryptor then enters the ciphertext into the prepared table column by column, starting with the column marked 1, continuing with the column marked number 2 until it has entered the entire text into the table. It then reads the plaintext in the rows of the table of the message.Our example:
The length of the ciphertext: 63
The length of the keyword (MYSTERY): 7 → 7 columns
63 : 7 = 9 → 9 rows
CIPHERTEXT:
IDNTS ZEEXT HORIG BEBSE UIOEC PXICJ AINTH ISOAC EIHRC HERYT AYCLT FAVRD ZUX
6 - VIGENERE CIPHER METHOD
(Polialphabetic Substitution Cipher)
* After most monoalphabetic ciphers were broken with the frequency analysis method, the search for a safer method has begun.
* French
cryptographer Blaise de Veginere developed Veginere cipher in 1586.
* This
method is a derivative of the Caesar technique. It's differenses from Caesar is
that it is shifted according to an unstable periodic number sequence.
Therefore, repeating letters correspond to another letter each time. In other
words, these cipher cannot be decrypted using the frequency method.
* Curriculum
topics related to Vigenere Cipher/ Aim: Sequences, Matrix, Permutation.We want
to increase your gains on these issues with Vigenere encryption activities.You
will experience interdisciplinary learning with history, mathematics,
informatics,music, English. Also you will learn new musics from partner
countries.By deciphering the message of a friend from another country, you will
collaborate and communicate by commenting on the messages.
HOW DOES IT WORK?
* A square matrix board of type nxn is used for the alphabet with n letters.The standart table is as follows
|
Vigenere |
PLAİNTEXT |
||||||||||||||||||||||||||
|
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
||
|
KEY TEXT |
A |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
|
B |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
|
|
C |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
|
|
D |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
|
|
E |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
|
|
F |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
|
|
G |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
|
|
H |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
|
|
I |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
|
|
J |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
|
|
K |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
|
|
L |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
|
|
M |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
|
|
N |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
|
|
O |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
|
|
P |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
|
|
Q |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
|
|
R |
R |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
|
|
S |
S |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
|
|
T |
T |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
|
|
U |
U |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
|
|
V |
V |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
|
|
W |
W |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
|
|
X |
X |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
|
|
Y |
Y |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
|
|
Z |
Z |
A |
B |
C |
D |
E |
F |
G |
H |
I |
J |
K |
L |
M |
N |
O |
P |
Q |
R |
S |
T |
U |
V |
W |
X |
Y |
|
Vigenere Board
(Tabula Recta)
There is a
common key text that the sender and recipient know. From the first row (first
horizontal) find the letters of the plain text, from the first column (first
vertical) find the letters of the key text, and then combined. Intersection
points create the encrypted text.
EXAMPLE
ENCRYPTION
If you want
to encrypt " HELP ME QUICKLY PLEASE" plaitext with the "NİCE
DAY"
|
Plaintext |
H |
E |
L |
P |
M |
E |
Q |
U |
I |
C |
K |
L |
Y |
P |
L |
E |
A |
S |
E |
|
Keytext |
N |
I |
C |
E |
D |
A |
Y |
H |
E |
L |
P |
M |
E |
Q |
U |
I |
C |
K |
L |
|
Ciphertext |
U |
M |
N |
T |
P |
E |
O |
B |
M |
N |
Z |
X |
C |
F |
F |
M |
C |
C |
P |
You find
"UMNTPEOBMNZXCFFMCCP" ciphertext.
Method:Vigenere,
Plaintext: HELP ME QUICKLY PLEASE, Keytext= NICE DAY, Ciphertext=
UMNTPEOBMNZXCFFMCCP
DECRYPTION
Decryption
can make simularly with Vigenere board. If you want decrypt ciphertext
"UMNTPEOBMNZXCFFMCCP" with
keytext "NİCE DAY"
|
Ciphertext |
U |
M |
N |
T |
P |
E |
O |
B |
M |
N |
Z |
X |
C |
F |
F |
M |
C |
C |
P |
|
Keytext |
N |
I |
C |
E |
D |
A |
Y |
H |
E |
L |
P |
M |
E |
Q |
U |
I |
C |
K |
L |
|
Plaintext |
H |
E |
L |
P |
M |
E |
Q |
U |
I |
C |
K |
L |
Y |
P |
L |
E |
A |
S |
E |
You find Plaintext: HELP ME QUICKLY
PLEASE










No comments:
Post a Comment